|
The goals of the ERE web page audit are to identify and make remedial recommendations for:
- Weaknesses of authentication which may allow unauthorized access, changes or defacement.
- Weaknesses within data capture fields and client authentication processes which make the page susceptible to hacking and to unauthorized access, particularly from the Internet.
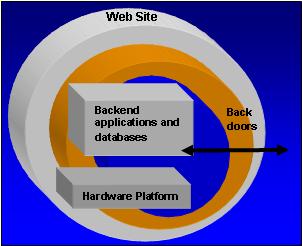
- Vulnerabilities within the authenticated region, which may pose threats to the backend applications and database(s).
- Weaknesses identified by web security testing of interfaces between the client facing application and the back-end applications and databases.
- Improperly secured administrative access to the web site including both the web software and the underlying hardware platform.
- Application security weaknesses identified by web application testing.
- Security lapses within the hardware platform.
Web Security Testing Steps
ERE Web Security Testing methodology is composed of web vulnerability scanning, web application testing, drill-down steps for auditing application security, and auditing the security of the architecture and platform(s) on which the web applications reside.
Our web application audits are a compilation of other components of ERE technology audits. Please refer to the other audit descriptions including:
|

