|
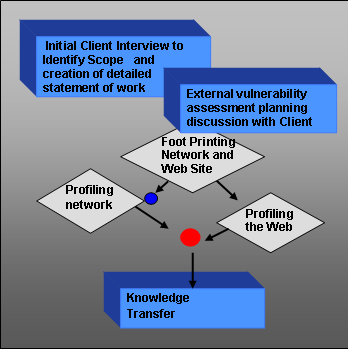
ERE identifies network vulnerabilities and exploits from a remote or external point of observation, in order to show how the network appears to a potential external predator.
This type of external audit is referred to by many diverse names such as ethical hacking, pen test, penetration test, external vulnerability assessment, an external VA, external risk assessment, perimeter security test, or a perimeter risk assessment.
ERE addresses the intent of all this technology jargon with our detailed audit of the perimeter of the enterprise network.
Vulnerabilities we Identify
- Network perimeter:
- Firewalls.
- Intrusion Detection and Prevention.
- Router settings.
- Web site security.
|
- Inside the network perimeter:
- Server settings.
- Patches.
- Authentication conventions.
- Tuning of anti-virus, anti-spam, and email content
filters.
|
- Remote access facilities such as terminal services.
- VPN connectivity.
- Encryption.
- Naming conventions.
- Network security architecture.
- Security policy.
|

Disruptive vs. Non-Disruptive Testing
ERE meets the need of any client by offering both types of testing.
- Non-disruptive penetration testing, which does not affect the availability of the network, as well as potentially disruptive penetration testing.
- Disruptive testing. While non-disruptive penetration testing provides the client with a list of vulnerabilities and recommendations of how to fix them, potentially disruptive testing actually tests the vulnerabilities to see if they can be exploited. ERE will provide at the client's choice, whatever mode of penetration testing best meets the client's needs.
|

