Firewall and VPN Audit |
 |
|
ERE perform integrated audits of firewall and VPN technology, focusing on four subject areas to test:
Rules, Objects, and IP Addresses
- Unique rule identification.
- Rule name identification.
- Assessment of rule compliance with security policy and with access policy for a VPN.
- Identify objects, both observed in event logs and not observed in event logs.
- Identify rules which are used and which are not used.
- Identify legacy rules which can not be used.
- Identify sanctioned source and destination IP addresses.
- Correlation of rules vs. objects.
- Identifying unused or legacy rules and objects.
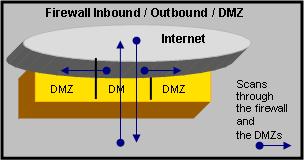
Scanning to Test Rules
- Scans from within DMZ’s to other DMZs and to inside the corporate network.
- Scans from outside the corporate network to inside the DMZs.
- Testing to determine if rules perform their intended roles.
- Testing to determine if rules exist to perform the intentions of policy.
Documentation
- Document all rules and their use.
- Create a dictionary of rules and objects.
Hardening Change Management
- Create a change management process for rules.
- Provide change management authorization document(s).
|
|
| |
Contact Us
905 764 3246
 |
| |
|
| |
|

