|
Intrusion Detection (IDS) has the ability to monitor network and server traffic in order to identify potential illicit activities such as malicious network traffic and computer usage that can't be detected by a conventional firewall.
This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, Trojan horses, and worms).
ERE provides state of the art host intrusion detection system monitoring service and network intrusion detection system monitoring service.
ERE will assess, design and implement the required monitoring infrastructure appropriate for each client’s specific environment. On an ongoing basis ERE will monitor the output from the sensors, analyze and forward alerts in a timely fashion and provide regular reporting. ERE will also help define an incident response process and provide technical resources to help resolve or recover from major incidents, as determined by each client’s specific requirements and processes.
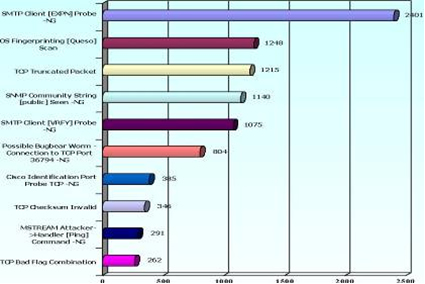
IDS Top 10 Attacks
Vulnerability Management
- We buffer our clients from the complexity and labour intensive effort to install and use intrusion detection.
- We constantly reduce false positives in order to save our clients time and reduce unnecessary network traffic caused by false positives.
- Maintain IDS software for patches and threat signatures.
- Provide crystal clear trouble tickets identifying root cause, risk, and remediation suggestions.
- Provide regular reporting about the security health of the network to both technical staff and management.
- ERE will help define and implement effective incident response processes.
Simple Painless Implementation
- ERE works with clients to determine requirements based on risks and current environment.
- Design the intrusion detection system configuration.
- Implement using existing hardware and IDS software or assist to evaluate and select the best fit IDS software and hardware.
- Document intrusion detection system operational activities and procedures.
- Work with our clients to define alert levels and corresponding response and escalation procedures.
Contact us right up front to save time and expense
The total cost of ownership of IDS may be far less than you expect. ERE’s monitoring service may dramatically reduce current or projected IDS costs. Let us save you time. Contact us for a cost saving quote.
|

